X-VPN's live transparency report turns no-logs claim into verifiable proof
In a sea of no-logs marketing, X-VPN delivers operational evidence to back it up

In a VPN market flooded with vague no-logs claims and one-time audits, X-VPN is taking a different path. The Singapore-based provider has launched a real-time transparency report that shows the inner workings of its privacy infrastructure.
This isn't just a PR move. The public-facing page displays a live feed of operational metrics, including law enforcement requests, bandwidth usage, and server specs. And unlike traditional whitepapers or delayed audit summaries, these updates happen continuously. This format turns a bold privacy promise into something anyone can verify.
This article unpacks how X-VPN’s approach is reshaping the no-logs conversation and what it signals to privacy-minded marketers and tech leaders.
Short on time?
Here is a table of content for quick access:
- What happened: real-time transparency, not one-time audits
- Context: what no-logs means in practice
- What marketers should know
Real-time transparency, not one-time audits
X-VPN's transparency report shares a wide range of data that most VPNs keep behind closed doors. Key metrics include:
- Legal and DMCA requests (2017–2025): The company has received multiple legal demands but has never shared user data, reinforcing its claim that no identifiable logs are retained.
- Bug bounty disclosures: Issues like authentication bugs and protocol flaws are logged by category, with public status updates that show how quickly they were resolved.
- Server and network performance: Bandwidth jumped from 80Gbps in 2017 to 386Gbps in 2025, with support for over 10 million concurrent connections. These metrics help verify that the infrastructure is both private and scalable.
- RAM-only architecture: All servers run with no attached storage. Session data is stored only in memory and wiped instantly after reboot, with no logs written to disk.
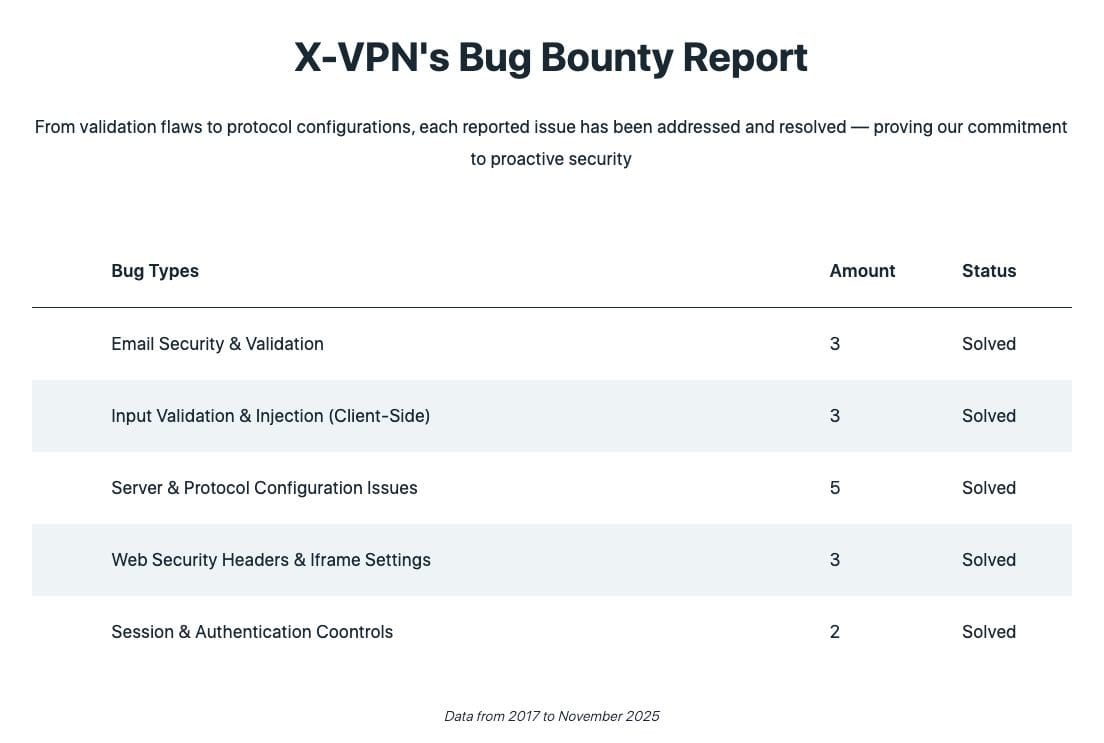
Each update helps validate a privacy model that avoids collecting or storing anything that could link traffic to a user. More importantly, the fact that these disclosures are ongoing allows users and security teams to monitor trends and behavior in near real time.
What no-logs means in practice
The VPN industry loves the term “no-logs,” but most users misunderstand it. It doesn’t mean zero data collection. Reviewers from PCWorld, Cloudwards, and TechRadar all agree: a true no-logs VPN does not store identifiable activity data like IP addresses, DNS queries, or browsing history. It may still collect basic operational data if it is anonymized, temporary, and never written to disk.
X-VPN aligns with that standard. According to its disclosures, it does not retain browsing history, device identifiers, location data, or even payment information. Traffic metadata is erased within seconds. Server binaries are verified on each reboot, and there is no way to reconstruct past user activity even if a server is seized.
By framing transparency as an ongoing process, not a marketing claim, X-VPN is trying to shift expectations across the industry.
What marketers should know
X-VPN's transparency initiative is more than just a technical win. It offers strategic lessons for privacy-forward brands and SaaS marketers.
1. Trust is a product feature now
Customers and compliance teams no longer trust blanket statements about data protection. What they want is proof. If your brand handles sensitive data or offers cybersecurity services, consider how you can turn internal transparency into public-facing trust assets.
X-VPN didn’t just say “trust us.” It published metrics that speak for themselves.
2. Continuous disclosure builds credibility
Annual audits and fine-print privacy policies are not enough anymore. X-VPN’s always-on format keeps trust current, not stale. Marketers in regulated or high-scrutiny sectors can learn from this. Live service updates, changelogs, or uptime trackers could be powerful additions to your brand narrative.
3. Words like “no logs” need backup
In cybersecurity messaging, terms like "secure," "private," or "compliant" carry weight. But using them without evidence is risky. The takeaway here is to define what your claims mean, then point directly to the systems that make them true. That is how you protect your brand while building stronger buyer confidence.
X-VPN’s new transparency report is not just a branding exercise. It is a structural move to make privacy auditable and visible, 24/7. For a sector built on trust, this kind of operational disclosure could become the new standard.
Whether you are marketing a privacy tool or evaluating one for enterprise use, this is the signal to watch. The future of privacy communication is not about promises. It is about receipts.



